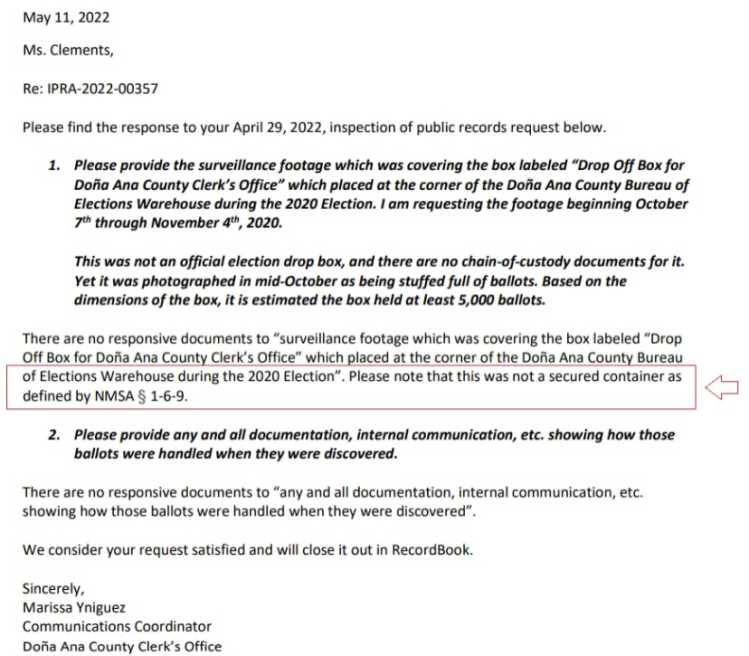
Perhaps one of the notorious examples of the vulnerabilities of election voting machines currently in use in our elections was on display during an episode of Conservative Daily. While this was not evidence of whether or not Dominion voting machines altered the vote, it is evidence that Dominion voting machines can be hacked and how. The video evidence they demonstrated during a live broadcast should at the very least place a moratorium on litigation against the defendents in the Dominion voting systems defamation cases until a thorough cyber forensic investigation into the machines and their electronic digital records can be examined in states elections in question. I published an article previously about this election fraud vulnerability on TheCReport.com (currently down). Here it is in case you missed:
Election Voting Machine Systems Confirmed:
Designed to Rig
Something occurred a while ago that should have taken note among the various alternative and independent news agencies in America. But it didn’t. The seemingly long belabored topic of election integrity coupled with the sacrilegious discussion of voting machine security went unnoticed. Perhaps it’s unfair not to say some had seen what they thought they’d seen before. A look back at the Antrim County, Michigan case from 2020 shows numerous similarities. Matt Deperno’s team was able to prove that Dominion Voting Systems, the machines used by the voters of Michigan in the 2020 election were vulnerable and that were there a bad actor with access to the machines the elections could be rigged. In the video, Jeffrey Lendberg whom we have also seen testify in the 2022 Otero County, New Mexico election case, demonstrates how a voter would never know the machine is vulnerable to attack. The truth, the fact every major media outlet, anti-American politician, judge, attorney, voter and businessman seems to ignore is the simple fact that the machines can compromise the vote of the people.

WATCH THE VIDEO:
Antrim County plaintiffs to introduce new evidence on voting systems
In the era where voting machine systems and those that own and manufacture them are sacrosanct as punishable by massive fines ordered by traitor courts that do not work for the people nor the preservation of these United States of America, on the internet broadcast Conservative Daily, audience members saw a group of patriotic Americans making another pitch to the American people about the security of security in our elections. In the OAN video Mr. Lendberg seems to share with us a method of rigging the vote by way of accessing some backdoor file pages and changing some numbers. Viewers of the Conservative Daily Show witnessed a similar example at the head of the presentation. The difference between the two presentations is an expanded understanding of how the voting system machines currently in use across these United States of America are not only vulnerable to corruption but were designed to give corruptibility to any individual who knew how to access the imbedded vulnerabilities. But Americans would never know because the voting machine companies, the courts and the anti-American politicians will not let us see the source code.
Designed to Rig: Demonstrating the Numerous Access Points Built into Dominion, ES&S and Hart InterCivic Voting Systems
Presenting the machines built-in access points on the Conservative Daily broadcast was a computer tech analyst named Mark Cook. Mark Cook was invited to investigate the Mesa County, Colorado Dominion Voting Systems machines used in the 2020 election. A copy, or an image, of the 2020 Dominion Voting System and database which included all data collected and retained from the 2020 election and other elections, had been made by then Mesa County Clerk, Tina Peters. Sharing with the audience the many methods one may use to manipulate an election via the software illegally installed on the voting system themselves, as well as the many means by which one may physically access these methods, one asks the question: were these machines created to make it easy to manipulate elections? Because there were so many ways to exploit the system should one way be sleuthed out didn’t necessarily mean it was the way the system was exploited.
The physical evidence shared on Conservative Daily should cause more than alarm. As I will share at a later point, this is a smoking gun, however the fingerprints on that gun may have been erased. As stated above, evidence of election fraud has literally been streaming at the American people since 2020 but the signal has been suppressed not only by the Lame Stream Media, but by the corporate-political, social-industrial complex. Mark Cook showed several different ways that the Dominion Voting System could be physically violated in order for a perpetrator to manipulate an election without evidence of the act ever taking place. The question of whether or not an election was rigged and stolen because of these machines is NOT important, the fact that IT IS POSSIBLE should cause county clerks from across these United States of America to suspend the use of ALL election voting machines systems immediately.
The first Red-Flag as presented is the inclusion of illegal-for-election-machine software not certified to be on an election system by way of SQL Management Studio. The software is known to be vulnerable, opening backdoor access to election data that can be used to read and manipulate the vote. Let the record reflect this uncertified software is installed by Dominion Voting Systems prior to shipping as disclosed by Mark Cook on Conservative Daily.
Viewers are next presented with a system by which a program can be delivered to the machine system that will run automatically and in seconds with no program log recording its presence or the changes the program ran may have made to the election data.
- The USB Drive
In a video demonstration, Mark Cook shows how easy it is to use a USB Drive to manipulate the vote. In it, Cook asks Conservative Daily host Joe Olstein to insert a USB drive into the computer that houses the Dominion election system software. When that happened, an automatic program ran that accessed the backdoor through the system and altered the election data—the votes. In this case, it flipped the vote. Any number of individuals in any number of roles with any motive could easily rig an election. Even an unsuspecting clerk can be told USB drives are simply used to transmit data and unknowingly participate in election crime. In the event there is protection software to guard against exploitation by USB drive, it has been discovered this measure can be overridden if the malicious USB drive contains code that cause it to appear to be a keyboard to the Voting Machine System. As we will discuss further at another time, USB drives were all but ubiquitous during the 2020 election season. The question is where have the USB drives vanished to and what programs were on them?
WATCH THE VIDEO
Mark Cook Demonstrates How a USB Drive Can Run Undetected Auto Program on Dominion Voting System
In another shocking example, Mr. Cook showed how the USB Drive could not only emulate a keyboard, but also has a built-in wireless access point. He connected his cell phone to the network the USB drive was connected and was able to load the interface to the Dominion Voting System image he was using to demonstrate the hack. He loaded values into data centers for the election results, clicked “run” on his phone and ran a program on the voting machine from his cell phone. Any criminal perpetrator of election crimes could potentially access and manipulate election results from their cellphone.
2. Phone Cords
While it was not demonstrated, it was explained that a phone cord plugged into a voting machine system could also be used to deliver the package of malicious software or run a malignant program all of which could subvert the vote/will of the people in place of the preference of the programmer that rigged the election. Whether the program was delivered through a rigged phone cord or through a phone that contained the program and appeared to innocently “charge” the phone, election officials and the public would never know that it ran a program that accessed the election data and altered the voting results.
WATCH THE VIDEO
Mark Cook Demonstrates How Cell Phone & USB Drove Can Manipulate Election on Dominion Voting System
3. Wireless Cards Built Into Dominion Voting Machine Motherboard
It has long been known that there are modems located in election voting machines. Dominion Voting Systems is just the first to boldly lie to their customers and more importantly to the American public while receiving the benefit of a complicitly ignorant court to make an example of its detractors and get away with it.
In 2020, Politico published an article about the voting machine company ES&S (Election Systems & Software). ES&S was rebuked by the federal agency over elections the Election Assistance Commission because they had deceptively marketed their voting machines to 89 clients indicating their voting machines with “embedded modems have been sanctioned by the EAC under its testing and certification program.”
The EAC agreed with the two election integrity groups and sent ES&S a letter in January indicating it was violating the EAC testing and certification program rules.
ES&S responded that it never meant to imply that the modem capability was certified, and said that regardless of what appears in the literature it always makes clear to states that the modem configuration is not EAC-approved. Nonetheless, the company agreed to remove all references to optional modems from its marketing documents.
But in a followup letter from the EAC on March 20, the commission indicated this was an insufficient remedy. It instructed the company to recall all misleading marketing materials already in circulation and to directly notify current and potential customers who received the “misrepresented information” that it had been inaccurate. It gave the company 15 days to do this.
“Failure to comply will result in the EAC publicly announcing that the voting system no longer complies with its original certification, and could include initiating decertification actions and/or suspension of manufacturer registration,” wrote Jerome Lovato, director of the EAC’s testing and certification program.
ES&S agreed to send a letter only to customers who use the DS200 with modems, informing them that the version is not EAC-certified, and to post a note to its customer portal advising the same. It indicated that the coronavirus could delay these efforts, though it would make “commercially reasonable efforts” to do this by April 15."
Election Commission Orders Top Voting Machine Vendor to Correct Misleading Claims” – Politico, Aug. 13, 2020
In 2021, it was reported during the Antrim County, Michigan case by the Matt Deperno team, the ES&S DS200 voting machines contained a Telit LE910-SV1 Modem Chip installed on its motherboard.
Modems and other wireless devices have been found to be either built into the motherboard or otherwise installed into the voting system. Whether reported by Politico or the New York Times, or alternative media, one factor that escapes the public is the amount of wireless devices built into the system. Unless the election official were tech knowledgeable and allowed access to inspect the machines, they would never detect one wireless device let alone multiples wireless devices. The question is, why so many?
Dominion Voting machines have also been found to have wireless devices. In 2022, the Mesa County Colorado Voting Systems: Forensic Examination and Analysis Report #2 showed there were 36 wireless devices found imbedded in the voting system.

The report found the Dominion Voting System may have lied had they ever claimed they could not connect to the internet and that their product “violates Voting System Standards (“VSS”) which expressly mandate prevention of the ability to “change calculated vote totals.” The investigators found the Dominion voting machine was “configured with 36 wireless devices which represent an extreme and unnecessary vulnerability, and which may be exploited to obtain unauthorized access from external devices, networks, and the Internet.” It should be noted that throughout the presentation by Mark Cook on Conservative Daily nothing in the Dominion Voting System acted to prevent further exploitation at deeper levels of the voting system.
Far more egregious than the actions enabled by the internal make-up of the voting machines is their ability to cover the digital tracks that, by federal and state law must be tracked, logged and retained for a statutorily predetermined amount of time.
An American Issue: The Corruption of Our Elections
Evidence of election corruption has been submitted to the American people in great stead since the rigged and stolen 2020 election took place. We have witnessed numerous ways to steal an election whether on the ground with ballot mills and traffic mules and unlawful get-out-the-vote funding or electronically by digital corruption and partisan courts and collusion, but the topic of election integrity gets the far-right slant due to the polarizing boost of the January 6th False Flag Riot. One of the underlying points that often goes moot in the MSM propaganda stream is that President Trump supporters showed up to Washington D.C. because the 2020 ELECTION WAS STOLEN. But the talking point falls back to focus on President Trump and all that matters is that his supporters were there, and he is right-wing, so they are right-wing.
In fact, both sides of the aisle favor the electronic voting machines. And both Democrats and Republicans should be concerned about the vulnerabilities of the voting machines. For one point, those found behind Dominion voting machines are individuals like Eric Coomer, CEO of the company who has openly supported Antifa and woke causes. Dominion voting systems has also had deep Democrat operatives like Marc Elias, with former Clinton ties, come to their defense. Conversely, Establishment Republicans support keeping voting machines in elections and deny any extensive election fraud could exploit the systems. In 2020, a left-of-center, never-Trumper by the name of Jennifer Cohn reported about the election voting system monopoly by the GOP via ES&S. An Establishment Republican organization known as the Council for National Policy had a founding member named Howard Ahmanson Jr. who contributed to the initial funding for ES&S (originally called AIS). She continues to report on the RINO funding organization to this day:
Counties Must Immediately Suspend Use of All Voting Machine Systems
The question of whether or not the 2020 or 2022 elections were rigged and stolen is not importance if one understands the severity of the situations enabled by the design of the voting system machines. Mark Cook delivers other means to manipulate the vote and reports on findings that could allow access to perpetrators both in the cyber realm and physically through the machines. The media has suppressed all stories, reports, investigations, proceedings, cases and hearings regarding election fraud and has championed election voting system manufacturers like Dominion Voting Systems. The courts have behaved curiously and, in some instances, contritely across these United States of America.
With the information presented on Conservative Daily, our knowledge of how pernicious the ability to exploit the voting machine systems we use in our elections today expanded and the topic resurfaces. It is being offered to Americans again to do something with this information. While diligent County Clerks may issue an emergency order suspending the use of electronic voting systems, we understand not many clerks are aware or onboard with any matter covered in this article, by Mr. Cook, or in any report previously issued regarding the vulnerabilities of electronic voting machines. We will have to educate our local election leaders on these findings and prompt them to suspend the use of the machines. Election officials, be they elected, appointed or hired, will not act unless they are prompted to and those prompting them to do so should be we, the people.
Watch the entire presentation on Conservative Daily’s Rumble page: